
Cybersecurity, UK PSTI, and ETSI EN 303 645
Overview of the PSTI Act
The UK's Product Security and Telecommunications Infrastructure (PSTI) Act is legislation aimed at enhancing the security of telecommunications infrastructure and products. This act specifically focuses on the security of Internet of Things (IoT) devices, mandating that all IoT products sold in the UK market meet specific security requirements. The goal of the PSTI Act is to reduce cybersecurity risks and protect consumers and businesses from potential security threats.

Introduction to the ETSI EN 303 645 Standard
ETSI EN 303 645 is a set of IoT security standards developed by the European Telecommunications Standards Institute (ETSI). This standard aims to provide a series of security guidelines for the design, development, and production of IoT devices. It includes a range of fundamental requirements, such as secure booting without passwords, minimizing the attack surface, and ensuring the security of device software updates, to ensure IoT devices can withstand cyberattacks and data breaches. ETSI EN 303 645 is a globally recognized cybersecurity baseline standard adopted or intended to be adopted by many countries worldwide. It has been officially integrated into the IECEE Scheme, making it a universally accepted standard beyond Europe. Soon, we will see CB reports adopting the ETSI EN 303 645 standard.
Relationship Between PSTI and ETSI EN 303 645
The relationship between the PSTI Act and the ETSI EN 303 645 standard lies in the fact that the PSTI Act provides the legal framework and specific requirements for IoT device security, while ETSI EN 303 645 offers the technical guidance to achieve this framework. In other words, the PSTI Act defines the "what" of IoT device security, and the ETSI EN 303 645 standard explains the "how" to meet these security requirements.
So, what are the requirements of ETSI EN 303 645 that must be met to comply with the PSTI?
There are three main points:
1. Prohibition of Universal Passwords: Avoid using universal passwords and adopt secure encryption methods. The focus is on secure authentication, requiring customers to properly apply security protection protocols for various ports and comply with internationally accepted encryption principles.
2. Implementation of Vulnerability Disclosure Management: Companies must establish a vulnerability disclosure policy that allows researchers and users to report potential security issues. This means that companies need to set up a public vulnerability reporting mechanism and commit to timely response and remediation of reported vulnerabilities.
3. Transparency of Product Security Update Services: Companies should implement a secure software update mechanism, including the use of signature verification for update integrity and source. Additionally, they should notify users of available updates and possibly offer automatic update options.
Conclusion
As IoT devices play an increasingly important role in our daily lives, ensuring their cybersecurity becomes crucial. The UK's PSTI mandatory certification act is a pioneer in the cybersecurity certification market, and more countries and regions are expected to standardize their cybersecurity certification requirements in the future.
China JJR Laboratory offers PSTI and ETSI EN 303 645 services.
Email:hello@jjrlab.com
Write your message here and send it to us
 Toy Toxicology Testing CA
Toy Toxicology Testing CA
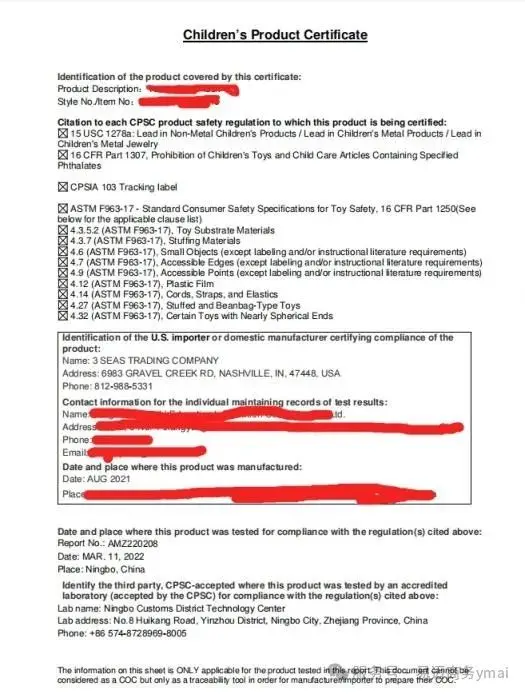 CPSIA Compliance for Children's Products
CPSIA Compliance for Children's Products
 Food Contact Items Testing
Food Contact Items Testing
 Energy Star Testing Laboratory
Energy Star Testing Laboratory
 Do I Need to Test Every Color for CPSIA Compliance
Do I Need to Test Every Color for CPSIA Compliance
 Accredited Medical Device Testing Lab
Accredited Medical Device Testing Lab
 Safety Testing for Baby Wrap
Safety Testing for Baby Wrap
 United States Electrical Plug Certification
United States Electrical Plug Certification
Leave us a message
24-hour online customer service at any time to respond, so that you worry!




